Can two people speak at the same time and still understand each other's statements? Well, not. The same goes for data frames in a computer network. If we transmit two frames at a time, they'll collide with each other, and data will get lost.
Before discussing Controlled access protocols, please refer to Random access protocols.
So how are controlled access protocols different from random access protocols?
The difference is, only that station can transmit the data which is approved by all other stations in that network. And we saw that in random access protocols, the transmission is based on the availability of the transmission channel.
So, here in controlled access protocols, only one station can transmit the data frames at a time, which leads us to a collision-free transmission through the communication channel.
Let us now discuss the types of controlled access protocols. There are three types of Controlled access protocols:
-
Reservation
-
Polling
-
Token Passing
Let's learn about them one by one.
Controlled Access Protocols
1) Reservation in Computer Network
Whenever we travel on a train or an airplane, the first thing we do is to reserve our seats, similarly, here a station must make a reservation first before transmitting any data frames.
This reservation in the Computer Network timeline consists of two kinds of periods:
-
Reservation interval of a fixed time duration
-
Data transmission period of variable frames
Consider there are 4 stations then the reservation intervals are divided into 4 slots so that each station has a slot. This means if n number of stations are there then n slot will be allotted.
Now let us assume that these 4 stations are 4 friends, now if friend-1 speaks in his slot-1 then no other friend can speak at this time. Similarly, if station-1 transmits a 1-bit data frame in slot-1 then at that time no other station can transmit its data frames and they must wait for their time slot. After all the slots have been transmitted and checked then each station knows which station now wishes for transmission.
The biggest advantage of this method is since all stations agree on which station is next to transmit then there are no possible collisions.
The illustration below shows a scenario with five stations with a five-slot reservation frame. here, in the time interval stations 1,3,4 are the only stations with reservations, and in the second interval, station-1 is the only station with a reservation.

2) Polling in Computer Network
Recall your school or college classroom, what was the first thing the teacher does after entering the class? The answer is roll call or attendance. Let's compare the scenario. The teacher calls roll number 1 and gets a response if he/she is present then switches to the next roll number, say roll number two and roll number 2 is absent, so the teacher gets no response in return or say a negative response. Similarly, in a computer network, there is a primary station or controller (teacher) and all other stations are secondary (students), the primary station sends a message to each station. The message which is sent by the primary station consists of the address of the station which is selected for granting access.
The point to remember is that all the nodes receive the message but the addressed one responds and sends data in return, but if the station has no data to transmit then it sends a message called Poll Reject or NAK (negative acknowledgment).
But this method has some drawbacks like the high overhead of the polling messages and high dependence on the reliability of the primary station.
We calculate the efficiency of this method in terms of time for polling & time required for transmission of data.
Tpoll = time for polling
Tt = time required for transmission of data
So, efficiency = Tt / (Tt + Tpoll)
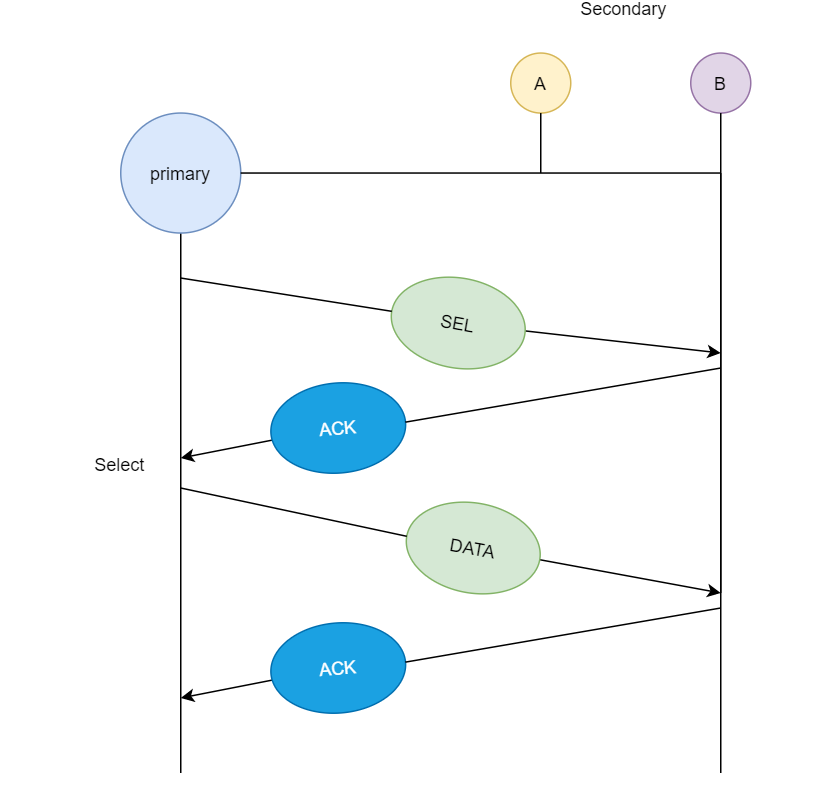
Whenever the primary station wants to receive the data, it asks the secondary stations present in its channel, this method is polling. In the first diagram, we see that the primary station asks station A if it has any data ready for transmission, since A does not have any data queued for transmission it sends NAK (negative acknowledgment), and then it asks station B since B has data ready for transmission, so it transmits the data and in return receives an acknowledgment from the primary station.

In the next case, if the primary station wants to send data to the secondary stations, it sends a select message, and if the secondary station accepts the request from the primary station, then it sends back an acknowledgment, and then the primary station transmits the data and in return receives an acknowledgment.
3) Token Passing in Computer Network
Now, say 4 people are sitting on a round table and only that person can speak who has the token. In computer networks, a token is a special bit pattern that allows the token-possessing system to send data or we can say that a token represents permission to transmit data. The token circulation around the table (or a network ring) is in a predefined order. A station can only pass the token to its adjacent station and not to any other station in the network. If a station has some data queued for transmission it can not transmit the data until it receives the token and makes sure it has transmitted all the data before passing on the received token.
This method has some drawbacks like duplication of tokens or sometimes the token being damaged or lost during circulation, or some times if we introduce a new station or remove an existing station from the network, this leads to a huge disturbance, which should be taken care of so that the efficiency of the method is not affected.
The performance of a token ring is governed by 2 parameters, which are delay and throughput.
Delay is a measure of the time; it is the time difference between a packet ready for transmission and when it is transmitted. Hence, the average time required to send a token to the next station is a/N.
Throughput is a measure of the successful traffic in the communication channel.
Throughput, S = 1/ (1 + a/N) for a<1
S = 1/[a(1+1/N)] for a>1, here N = number of stations & a = Tp/Tt
Tp = propagation delay &Tt = transmission delay
In the diagram below when station-1 possesses the token it starts transmitting all the data frames which are in its queue. now after transmission, station-1 passes the token to station-2 and so on. Station-1 can now transmit data again, only when all the stations in the network have transmitted their data and passed the token.

Note: A token can only work in that channel, for which it is generated, and not for any other.
Conclusion
Controlled access protocols play a crucial role in managing access to shared resources in computer networks. Reservation, polling, and token passing are three widely used techniques for implementing controlled access protocols. While each of these techniques has its advantages and disadvantages, the choice of the protocol ultimately depends on the specific requirements and characteristics of the network.
By using these protocols effectively, network administrators can ensure fair and efficient access to shared resources while minimizing the risk of collisions and congestion.
Frequently Asked Questions
1. What is a controlled access protocol?
A controlled access protocol is a technique used to manage access to shared resources in a network.
2. What is reservation in controlled access protocols?
Reservation is a technique in which a user reserves the resource before accessing it, ensuring exclusive access.
3. What is polling in controlled access protocols?
Polling is a technique where a device checks for the availability of the resource before accessing it.
4. What is token passing in controlled access protocols?
Token passing is a technique in which a token is passed from device to device, ensuring exclusive access to the resource.
You may also like: